ROTATING RESIDENTIAL PROXIES
Special Rotating Proxies
Rotating residential proxies with worldwide geo targeting optimized for high success rates.
Basic Rotating Proxies
Rotating residential proxies with random geo location.
Fast Rotating Proxies
Rotating residential proxies with worldwide geo targeting optimized for scraping and data gathering.
On Demand Proxies
Residential proxies with on demand rotation, geo targeting using user and password authentification.
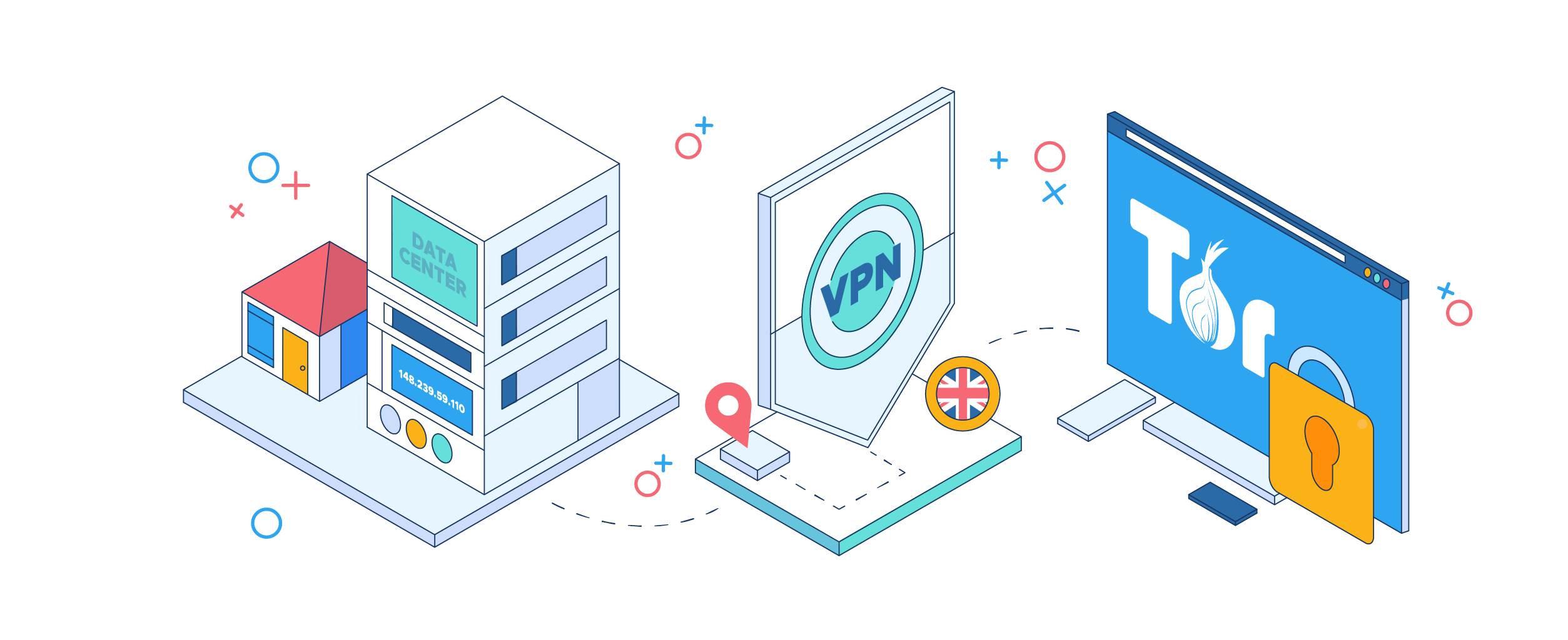
What are the main differences between Proxies, VPNs, and TOR?
The online environment is a big space that shelters not only valuable information for business purposes but also hidden dangers for those exploring its secrets.
For this reason, users go to great lengths to cover their tracks and keep private details safe from prying eyes on the Internet.
To do just that, a variety of tools and methods have been imagined to help users mask their IP addresses or encrypt the data they send and receive in the virtual world. Some of the most popular online means to reach information and remain safe is to take advantage of proxy server solutions, VPNs, or the privacy browser TOR.
But how different are these solutions from each other and which one(s) do you need for your business purposes?
As with anything else in life, it all depends on what you need to do. If you represent a company that is involved in data extraction jobs for business projects, you need a reliable proxy server solution.
However, if your company’s employees need access to online locations that require a higher level of security and privacy, then you may look for a VPN solution.
If proxies are usually considered by companies that need to extract large amounts of data from the Internet, VPNs and TOR are specially designed to offer a higher level of protection in the online environment for work-related activities and private browsing.
Let’s find out what each privacy tool can be used for so that you may better understand when to use a proxy server solution, a VPN product, or TOR.
What is a Proxy and when to use one
From a general point of view, when talking about proxies we have to imagine a connecting doorway that keeps the communication open between our systems and the remote sites we access while masking our IP addresses.
Companies that choose a proxy server solution to browse online connect to various resources by using an IP address provided by a data center or a residential user. With the new IP address acting as an online interface, companies engage in data scraping operations to obtain valuable data for their projects.
Now, we have to emphasize that not all IPs are the same and it’s important for a company - looking to obtain online content - to choose the right proxy server solutions from an established company in the field that comes with the necessary experience to recommend the right products.
For instance, though datacenter proxies represent the more popular choice for web scraping activities - since they provide speed and are easy to acquire - over the last years we’ve seen an increasing number of companies looking to obtain content from the competitors’ sites by relying on the anonymity provided by residential IPs.
The content the companies target usually becomes a vital part of their marketing and sales strategies and, to acquire the necessary data, these enterprises go to great lengths. And when you need to get the job done, the favorite ‘weapons’ of choice are always the genuine IP addresses that belong to home network users.
Residential IP addresses may not be as fast as the IPs delivered by data centers (in countries with fast Internet connections), but since they belong to genuine people they manage to offer a more reliable appearance removing the possibility of users getting blocked by web anti-scraping mechanisms.
Proxies may not provide the same level of security as VPNs or TOR, but they are an excellent choice for companies that want to scrape data from the online environment for business purposes.
What is a VPN and when to use one
A VPN (Virtual Private Network) solution is considered to be one of the most secure methods to go online for private and work-related reasons.
Users who choose to go online with a VPN product access a remote server from another country to reach the desired locations while hiding their own tracks from outside parties.
Further on, a VPN solution creates a secure tunnel to encrypt the data we send and receive online, which is an excellent method to avoid surveillance agencies and malicious actors who intend to track our activities.
For someone trying to analyze a user’s network traffic, all they can see is the established connection to a remote VPN server, but no actual details of the data we send and receive.
For all the ‘benefits’ provided by VPNs, these solutions are sometimes preferred by people who reside in authoritarian countries that keep the Internet under surveillance or by individuals who need to escape the watchful eye of law enforcement agencies that track their activities for political reasons.
At the same time, companies that allow employees to work from remote locations - and need to make sure they access work-related materials and resources in complete security and privacy - install VPN products on their devices.
Since a VPN filters all incoming and outgoing data traffic on the system, including applications, programs, system updates, and browsing data, we can definitely say that VPNs offer a high level of online protection.
But how good is a VPN for data scraping jobs? Well, though it’s obvious that web data can be accessed with VPN products, we have to remember that since we are dealing with encryption protocols it is difficult to obtain the same scraping speeds as we would get by using proxy server solutions.
For normal browsing activities and work-related stuff, VPNs are great. However, for resource-intensive data scraping tasks where bandwidth and connection speed are of the essence, you may have to choose a datacenter or residential proxy.
On our blog, you can read more about proxy vs VPN.
What is TOR and when to use it
When talking about TOR, many people start fantasizing about action movies where IT geniuses target banking sites and engage in crypto-related transactions running away from the FBI and other major law enforcement agencies.
In reality, things take place in a different manner as the TOR privacy browser manages indeed to offer the required privacy and security to users but at the cost of speed.
That’s because TOR - aka The Onion Router - works by stripping away a user’s private details and encrypting the data through a number of online nodes.
As the data is sent through the network of nodes, it is further encrypted and decrypted along the way, so that when it arrives at the destination it is almost impossible to tell who the user is and where he (or she) is located.
TOR privacy browser has become well-known for being used by social and political activists who want to keep underground activities secret from the national governments in their own countries.
Now, the main question arises: how good is TOR for data scraping activities?
Though we can definitely say that TOR is one of the most popular privacy-focused tools for people looking to remain safe, it is very difficult to recommend TOR for data scraping activities as it is simply too slow. For data extraction projects, proxy server solutions remain the main choice for companies that want to get the job done.
Proxy, VPN or TOR: what works best for data extraction projects
We've emphasized several times already in our article that proxy server solutions work best for data extraction projects as there are many companies that need to access and download large amounts of data.
And to do just that, these companies do not have the necessary time and resources to use VPN solutions that come at high costs and are not as fast as proxies. Though we may indeed argue that VPNs and TOR are more secure, these applications or tools are not suitable for web scraping activities.
Further on, we need to establish that in the online environment, the user - no matter whether we talk about a private individual or a company - is always forced to find the best trade-off between data access and online privacy.
More privacy and security in the online environment could impose not only higher costs, but may even lead to slower connections as the information needs to pass through multiple filters in order to be checked and verified, encrypted, or decrypted along the way.
Though all companies appreciate more Internet security, there is always a compromise between data access and online privacy. And when we refer specifically to data extraction and web scraping, companies that are involved in this area of interest always choose the power of datacenter and residential proxies to target the data they need.
Thus, we have to add that companies looking to obtain data from online sources via proxy server solutions have no problem using - at the same time - VPN products for increased security when accessing work-related materials.
VPNs and proxies can be used by the same company for various purposes and on different occasions. TOR is not so often used by companies since it’s not so fast and it does require some time for configuration, so the famous privacy browser is generally preferred by users who look for complete privacy.
Most of the time, enterprises that need to obtain data from online sources or look to protect their assets from online threats are already aware of what works best for them.
Proxy, VPN or TOR?
When looking to acquire web data, they choose the power of proxy server solutions. When they value the privacy and security of the data they have already acquired, they go for VPNs or TOR.
This category's latest stories

4 Simple Reasons Businesses Love To Use Proxies
Businesses love proxies for many reasons. In this article, we focus on the most important benefits for SEO, social media, online sales, and pricing.

What are Datacenter Proxies and How They Can Help your Business
Do you want to find out how datacenter proxies can support your business development? Check out our article and find out how they can support business!

6 Myths About Proxy Server Solutions
Are you aware of all the myths that surround proxies? Let’s debunk the most popular myths about proxy server solutions. Check out our blog post!
Featured Articles

News
02.12.2024
Introducing Ice Payments on Shifter
Discover seamless crypto transactions with Ice payments on Shifter. Streamline your proxy service purchases and unlock new opportunities with Ice integration.

Residential Proxies
04.04.2023
8 Myths About Proxies. What You Should Know?
Are you aware of all the myths and stories surrounding proxies? Check our article and test your knowledge of proxies’ true limits in the online environment.

News
03.21.2023
Looking for an Alternative to Pi Network? Why ice Network is the Perfect Solution
Find more about the tremendous advantages of the ice Network and mining ice coins, as many are starting to take notice, ultimately choosing to leave Pi Network to have access to better, more rewarding opportunities.
Shifter's legacy
Shifter was founded in 2012, as one of the first residential proxy providers, since then it has become one of the leading proxy networks in the world and it's used by more than 25.000 clients including Fortune 500 Companies. Users can connect from anywhere to access local data without any restriction, while preserving a high degree of privacy and security.